Balancing Cybersecurity Costs and Reality: How HUB ICT Contained a Cyberattack
Learn how HUB ICT's hybrid cybersecurity model successfully contained a sophisticated cyberattack in minutes, proving that strong security doesn't have to break the budget.
Cybersecurity solutions like CrowdStrike Falcon Complete provide world-class, fully managed, 24/7 protection. It's an incredibly powerful way to defend against threats — but the reality is, not every organisation can afford this level of service.
At HUB ICT, we understand this challenge. That's why we work with clients to tailor hybrid models that balance cost, practicality, and security strength. Recently, one of our major manufacturing clients faced a serious cyberattack — and our approach proved its value.
The Incident: A Real-World Cyber Breach
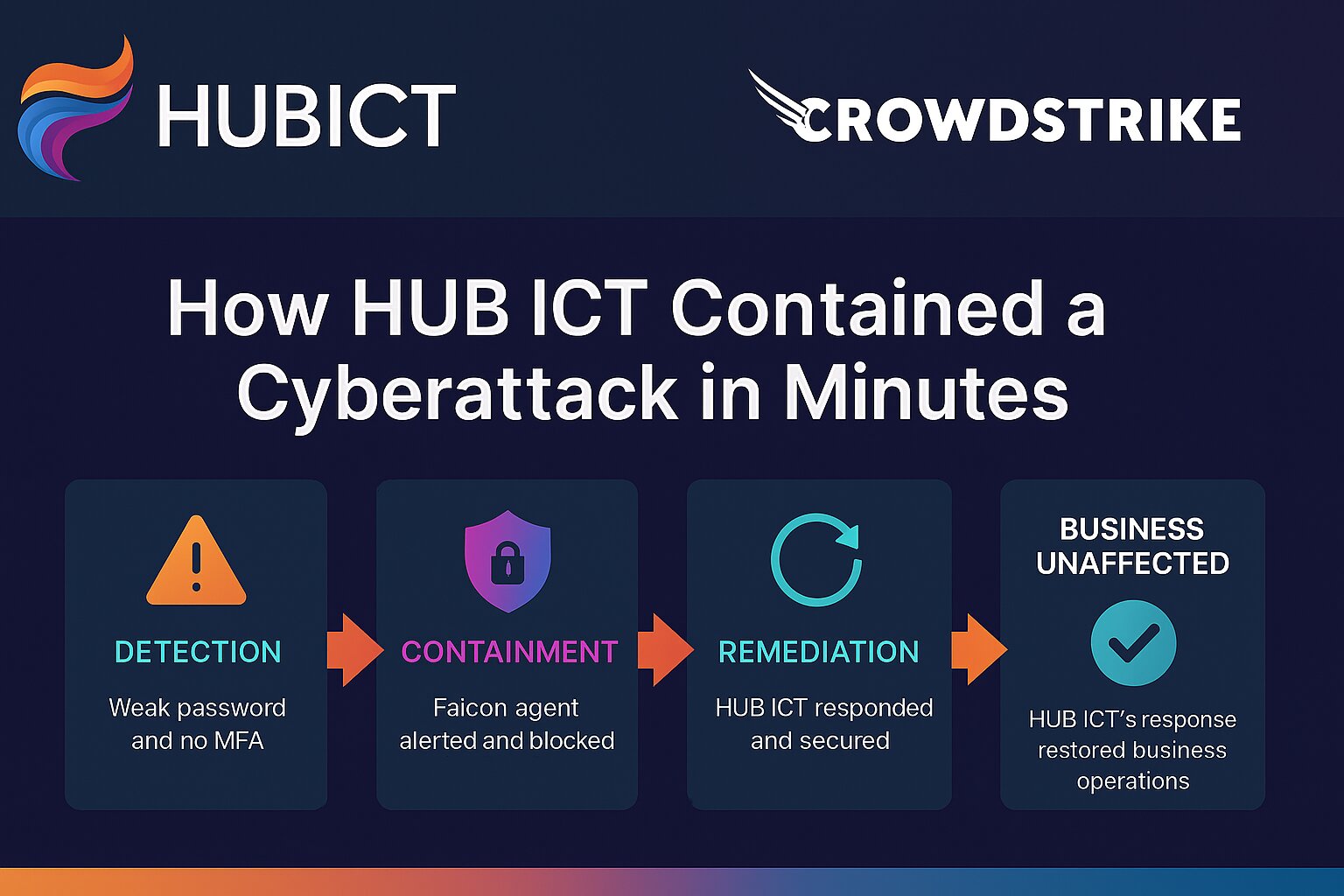
It started with a simple, yet all-too-common weakness: a weak password and no multi-factor authentication (MFA).
This gave the attacker an entry point through the VPN. Once inside, their actions escalated quickly:
- Running remote reconnaissance scripts to map the environment and identify stored credentials.
- Attempting to access the NTDS.DIT file, which holds Active Directory credentials — a goldmine for attackers.
- Deploying tools to crack hashed passwords and expand access.
- Attempting to install a Cloudflare Tunnel to maintain stealthy, persistent remote control.
This chain of events could have led to a catastrophic data breach and operational disruption.
But that's not what happened.
CrowdStrike Falcon: First Line of Defense
The CrowdStrike Falcon agent deployed on the client's endpoints was critical in stopping the attack before it spread.
- It flagged the suspicious activity in real-time, alerting our security team within minutes.
- It intercepted data flows, giving us visibility into exactly what the attacker was trying to achieve.
- It blocked the Cloudflare Tunnel installation outright, preventing the attacker from gaining persistence.
- Falcon's OverWatch intelligence provided immediate recommendations on where to look deeper.
Without Falcon in place, this attacker could have silently embedded themselves into the client's systems — with devastating consequences.
HUB ICT Cyber Team: Rapid Response & Containment
The difference-maker was speed. Within 10 minutes of the first alert, our HUB ICT cyber team was already in action.
Here's how we handled it:
- Immediate Containment – We isolated the affected systems and blocked the attacker's access, ensuring no lateral movement.
- Deep Investigation – Using the telemetry from Falcon, we mapped the attacker's steps, identified attempted credential theft, and confirmed no data exfiltration occurred.
- Remediation – Weak credentials were reset, MFA was enforced, and vulnerable configurations were hardened.
- Client Assurance – We provided the client with a detailed incident report and clear next steps — all while ensuring their day-to-day operations continued without interruption.
The client's experience? Business as usual. They didn't even realise an attack had been underway until we presented the incident response findings.
Falcon Complete vs. Our Hybrid Model
Here's the reality:
- Falcon Complete would have been the easiest and most convenient option. CrowdStrike's global SOC team would have managed everything, 24/7, end-to-end.
- But the cost of Falcon Complete can be prohibitive for many organisations.
That's why HUB ICT delivers a hybrid model:
- CrowdStrike Falcon agent & OverWatch provide the best-in-class detection and blocking.
- HUB ICT's cyber experts act as the dedicated response team — familiar with the client's IT environment and able to act fast when it matters most.
This model ensures robust protection at a more accessible price point, without sacrificing security outcomes.
Pros and Cons of a Hybrid Approach
Pros:
- Cost-effective compared to fully managed services.
- Combines powerful tooling with local expertise and response.
- Flexible and adaptable to organisational needs and risk levels.
Cons:
- Requires trusted in-house or partner response capability.
- Not fully "hands-off" — organisations must be engaged in the process.
- May not suit businesses with no IT/security maturity at all.
The Bottom Line
This incident is proof that you don't need to break the budget to be secure. With the right balance of technology and expertise, you can defend against sophisticated attacks and keep your business running smoothly.
At HUB ICT, we help organisations find that balance. Whether it's a hybrid approach like this one or a fully managed service, our goal is to ensure that cost doesn't become a barrier to strong cybersecurity.
💡 Is your organisation trying to balance security vs. budget? Let's talk about how we can build a model that works for your reality.
Secure Your Business Today
Don't let cost become a barrier to strong cybersecurity. Let's discuss a security model that works for your budget and business needs.